
Paige Spiranac makes hilarious 'eye contact' quip about Phil Mickelson, fans ask 'can you blame us'
Paige Spiranac starts the British Open with a 'eye contact' joke about Phil Mickelson
2023-07-21 17:57

Inclusive, Provocative...and Downright Horny, Baldur’s Gate 3 Gets Sex Right
Baldur’s Gate 3 is one of the hottest PC titles of the year, and no,
2023-10-03 23:24

NewLink and Dubai Chambers Forge Strategic Partnership to Support Bilateral Innovation Exchange and Collaboration
BEIJING--(BUSINESS WIRE)--May 27, 2023--
2023-05-27 12:59

U.S. forms team to set strategy on flying air taxis
By David Shepardson WASHINGTON (Reuters) -The Biden administration said Tuesday it has formed an interagency team to develop a national
2023-05-16 22:16

10 of the best JavaScript courses you can take online for free
TL;DR: A wide range of free JavaScript courses are available for free on Udemy. Learn
2023-07-09 12:25

British consortium to invest $9 billion in Indonesia mining, EV batteries, minister says
JAKARTA A British consortium that includes mining giant Glencore will invest about $9 billion in Indonesia's mining and
2023-05-31 17:53

Scientist shares routine that can 'make you better at everything'
The emphasis on a good night's sleep is nothing new. But now, neuroscientist, Dr Andrew Huberman, has shared one routine that he suggested can make you "better at everything." In a YouTube talk on After Skool, Dr Huberman said he immediately starts his day with a sunrise walk at 6.30am. "Getting outside for a 10-minute walk or a 15-minute walk is absolutely vital to mental and physical health," he shared. Despite coffee being the get-up-and-go drink for most, Huberman says the first beverage he consumes is salty water, as he claims it helps improve bodily functions. "There are certain foundational behaviours - certain dos and don'ts that set the stage for you to be better at everything," he continued. "It always comes back to two elements - that's sleep and what I call non-sleep deep rest. Sleep is the fundamental practice or part of our 24-hour cycle where if you don't get it on a consistent basis, you are down-regulating your ability to do everything." He went on to discuss a "90-minute bout of work," in which he says he turns his phone off to fully optimise this time. "You'd be amazed how much you can get done in 90 minutes if you are focused," he said. Huberman then ensures he gets in an hour's worth of exercise before exposing himself to cold temperatures such as an ice bath. The NHS states that there are no official guidelines regarding how much sleep a person should get each night as everyone is different. "On average, a 'normal' amount of sleep for an adult is considered to be around seven to nine hours a night. Children and babies may sleep for much longer than this, whereas older adults may sleep less," they wrote. Sign up for our free Indy100 weekly newsletter Have your say in our news democracy. Click the upvote icon at the top of the page to help raise this article through the indy100 rankings.
2023-08-25 21:58
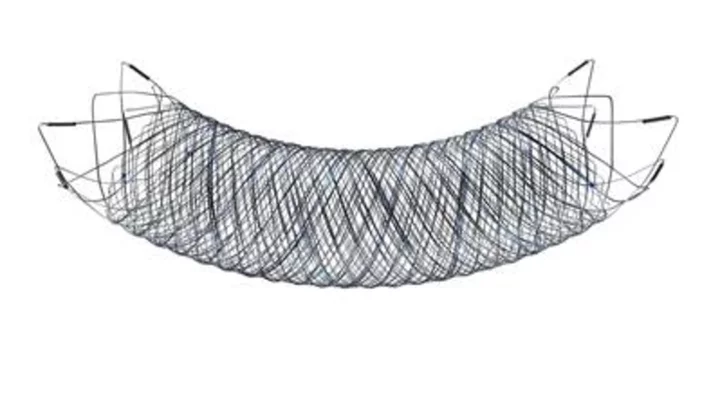
MicroVention Celebrates One-Year Anniversary of FRED™ X Flow Diverter with Over 1,000 Patients Treated Across the U.S.
SAN DIEGO & ALISO VIEJO, Calif.--(BUSINESS WIRE)--Jul 31, 2023--
2023-07-31 21:29

Deezer to detect AI-generated music clones
Music streaming app Deezer said Tuesday it was launching a tool to detect and tag songs with AI-generated vocal clones in a bid to protect...
2023-06-06 18:17

Bethesda boss Pete Hines hits back at claim Starfield start menu was 'hastily' designed
Pete Hines insists the 'Starfield' main menu has been designed "differently" to other game menus.
2023-08-21 19:24

Paysend and Visa Strengthen Their Strategic Collaboration to Help Transform Global Money Movement
LONDON--(BUSINESS WIRE)--Sep 14, 2023--
2023-09-14 19:26

Canon imagePrograf TC-20M Review
The Canon imagePrograf TC-20M ($995) is the first under-$1,000 24-inch wide-format printer with a built-in
2023-06-25 10:52
You Might Like...

The 15 Fastest EA FC 24 Ultimate Team Players at Launch

ISACA Welcomes New CEO Erik Prusch

Every single person in Europe is a descendant of one man

Tristan Tate slams journalist amid alleged COVID vaccine connection to Shane Warne's death, Internet says 'stupid anti-vaxxer'

23andMe says hacker appears to have stolen people’s genetic information

Test scores for 13-year-olds drop several points since the start of pandemic, building on decade-long decline, report says

Roberta Nelson Shea from Universal Robots Receives Prestigious Robotics Award for Contribution to Robot Safety

DMs may come to Threads soon as Meta’s app now has one-fifth of Twitter’s user base
